This whitepaper outlines the security protocols Kadence uses to secure our system and protect our user’s privacy.
The way we work has changed forever. Kadence is on a mission to improve synchronization of people, space and time, creating the best conditions for people to thrive in the new era of work.
Kadence provides workplace leaders with an operating system to empower teams to make the best choices about how, when and where to do their best work, delivering data-driven insights into how people use spaces like desks and rooms.
Reliability
We are constantly monitoring our system and responding rapidly to any interruptions or issues. This allows us to commit to a system availability of 99.9% via our standard SLA, which equates to a maximum of 8 hours 46 minutes of downtime per year.
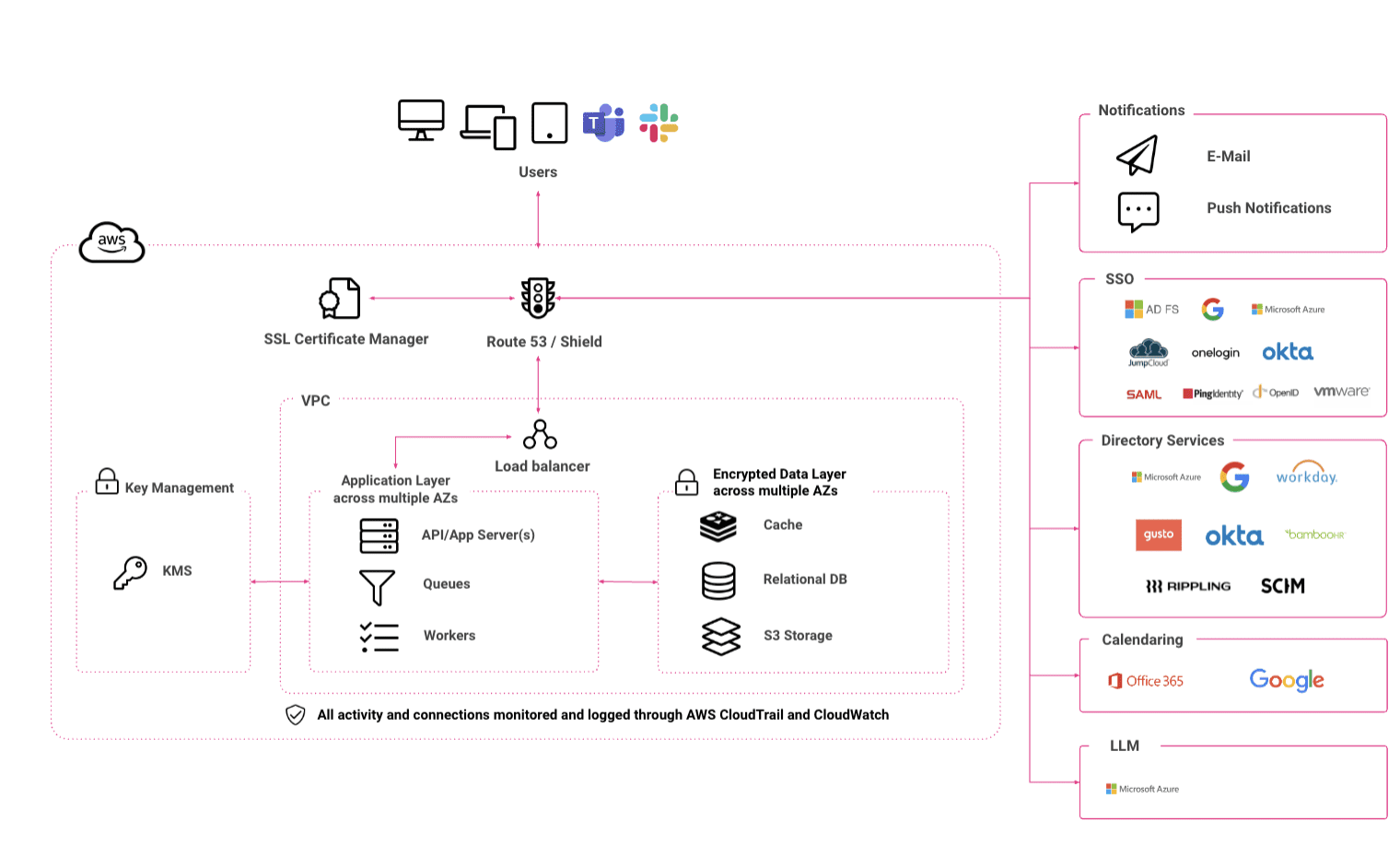
Data storage & residency
Our Cloud platform is hosted by Amazon Web Services (AWS) and provides a strong level of security in retaining our data. For more information about secure data storage, please refer to AWS security and AWS Certifications. All of our production data centres are hosted in the EU.
Data encryption
All of our customer data is encrypted in transit and at rest with all connections to our Cloud platform and protected via HTTPS/TLS 1.2+.
All passwords are salted and hashed using a one-way encryption algorithm for further protection, should an attacker gain access to a running instance. It is not possible to recover a stored password, these can only be reset through our ‘Forgotten Password’ process.
Data Tenantisation
Our multi-tenancy solution achieves data isolation with the use of row-based separation. We have strict control measures in place to eliminate the risk of customer data being exposed beyond its own tenant.
Data privacy
We take our responsibilities towards your data seriously; we will only store data that is absolutely necessary for the functioning of our solution. When a user is removed from the platform, all of their personally identifiable information will be permanently and irretrievably removed. We then anonymise all their usage data for trend and historical analysis. Our Data Privacy and GDPR policies are all available here
Data removal & decommissioning
All customer data is held in the AWS Data Centres in the EU. AWS has high standards in relation to installing and decommissioning hardware with decommissions media using techniques detailed in NIST 800-88. More information on this can be obtained here
Penetration testing
All our systems are penetration-tested annually by independent third party specialists. Any vulnerabilities discovered are tracked and addressed as a matter of urgency. Access to our latest penetration test reports are available on request.
All our mobile applications are tested to the OWASP MASVS standard.
Development & deployment process
At Kadence, we have robust development and deployment processes that ensure not only high quality code, but also high level of security for our product. Highlights of this process include:
- Static analysis of our code to catch issues before committing to our codebase.
- All code is peer reviewed and tested.
- Automated unit and integration tests to catch issues before deployment.
- Complete isolation of production, staging and development environments with principles of least privilege applied to each.
- Regular patching of all infrastructure to ensure we have addressed all known security issues with our technology stack. An independent SSL report on infrastructure is available here
API Access
Access to our API is controlled through rate limited API tokens. These tokens are unique to each tenant and are granted specific scopes at the creation time. It is possible to add and remove specific scopes, or decommission a token at any time through our Cloud platform.
Certifications
Kadence has successfully achieved SOC 2 Type II compliance and audit attestation. We have continual monitoring of our systems, platform, and security controls and are notified if anything drops out of compliance. We have also received Cyber Essentials certification. In addition, all of our infrastructure partners are SOC 2 and ISO 27001 certified.
Disaster recovery & Incident response
Kadence has detailed plans in place to enable disaster recovery and business continuity in the event of a significant incident. These plans can be made available to customers upon request.
Network architecture